OTD Blog | March 2021
HOW TO PREVENT RANSOMWARE ATTACKS IN THE INDUSTRY?
Ransomware hit Westrock and other industrial organizations. OTD BİLİŞİM specialists shared the ways to prevent ransomware attacks on industrial networks.

OTD BİLİŞİM specialists gave information about the ways to prevent ransomware attacks on industrial networks.
WestRock operations conducted at the $ 17 billion packaging firm were intervened by a ransomware attack that impacted the IT and OT (operational technology) networks earlier in this week. And two days later, a ransomware attack was realized against Dairy Farm Group which is a large $ 27 billion chain operator, and the attackers demanded a $ 30 million ransom
, which are just an example of tthe successful attacks of this week.
We have been witnessing daily attacks which have impact on OT networks resulted from BT since the outbreak of Wannacry & NotPetya ransomware attacks in 2017. The US National Security Agency (NSA) has also highlighted this for this very simple reason, which has worked.
STUDIES ON RANSOMWARE
Even though it is not an end at all, it is the most simple way to explain why ransomware attacks has increased dramatically over the past year. According to PurpleSec's latest report, the number of ransomware attacks has increased by 350 percent since 2018, the average ransom payment has increased by more than 100 percent this year while the downtime has increased by 200 percent, and the average cost per incident has been increasing as well.
Threat actor groups with names such as Egregor, Conti, Ragnar Locker Ryuk and many others are brutal, well funded and they are very willing to target anyone to get paid from COVID-19 vaccine producers, manufacturers, automotive manufacturers to critical infrastructure, governments and hospitals. In deed, the first random-related death occurred last September when German hospital was infected with ransomware and prevented the patients from being treated during the pandemic.
As a part of SCADAfence’s mission to protect the life and safety of civilians, we have prepared this guideline to help you prevent ransomware in your industrial organizations.
RANSOMWARE ENCRYPTION PROCESS
Let’s get back to the beginning and consider how these attacks do encrypt systems.
We have learned from the previous ransomware attacks we searched that attackers can encrypt the entire network within a few hours of their first access. In other cases, attackers would have to spend more time to evaluate which assets they wanted to encrypt and make sure to access important servers such as storage and application servers.
Most of the ransomware attacks which we learned from the newspapers try to end antivurus operations to make sure that their encryption processes will not be interrupted. It has been advanced by ending the latest ransomware types such as SNAKE DoppelPaymer VE LockerGoga and even the OT-related processes such as SIMATIC WinCC, Beckhoff TwinCAT, Kepware KEPServerEX and the OPC communication protocol , which interrupted the industrial process, and this increased the chances of victims paying the ransom. Such ransomware attacks have been seen in recent Honda and ExecuPharm attacks.
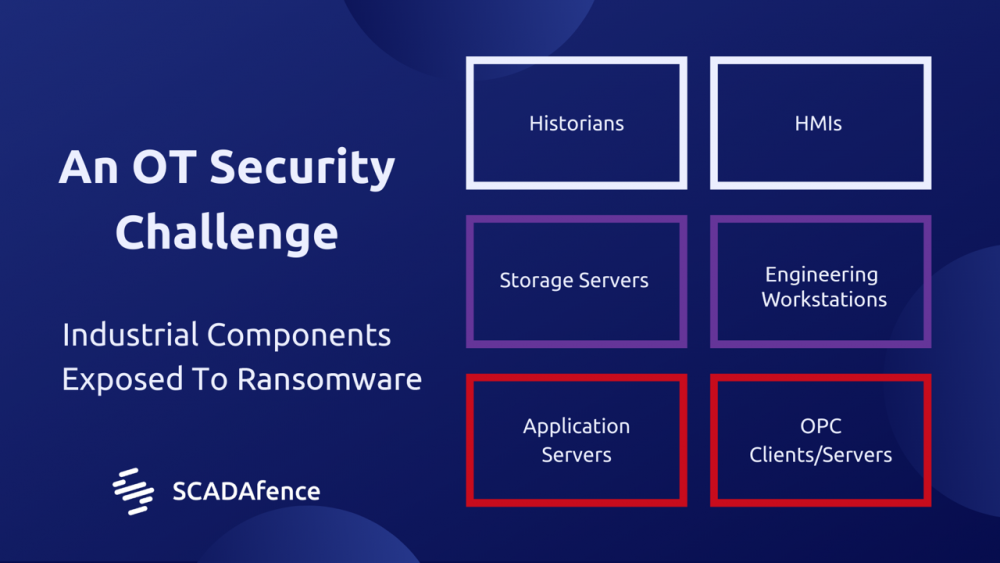
Scheme # 1 - An OT Security Issue: Industrial Components Subjected to Encryption
As we see, ransomware usually encrypts Windows and Linux machines. And we have not seen any encrypted PLC yet. On the other hand, many industrial services such as historians, HMIs, storage, application servers, management portals and OPC client (s) are run on Windows / Linux machines.
In many cases, ransomware processes will not stop on the IT network and will also attack OT segments. More encrypted devices mean a higher demand for monetary ransom from attackers. Organizations should be able to monitor and detect the threats at the IT / OT boundaries in order to effectively identify the risks before they get to the process-critical endpoints.
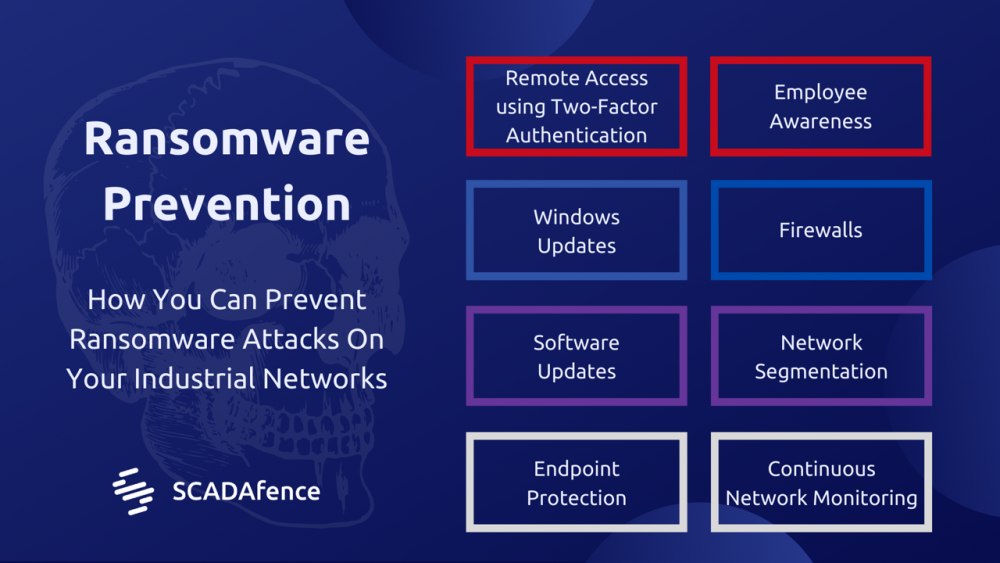
Scheme # 2 - Prevention of Ransomware: Preventing Ransomware Attacks on Your Industrial Networks
Some tools and techniques used by ransomware operators are at the level used by nation-state threat actors in targeted espionage campaigns.

Scheme# 3 - Tactics, Techniques, and Procedures Most Commonly Used in Ransomware Attacks
We recommend that organizations follow these common security procedures to minimize the risk of ransomware infection at every step of the kill chain:
FIRST ACCESS:
1. RDP
a. If possible, change RDP with a remote access solution that requires two-factor authentication which is supported by most VPNs now. So, it requires the attackers to be authenticated, for example with a code sent via SMS.
b. If you prefer to continue using RP, make sure that Windows Update is enabled and running.
2. Email Phishing
a. Train the organization personnel about the phishing. Personnel should be suspicious of inaccurate emails and should not click on suspicious links.
b. Install an anti-phishing solution.
3. Software Vulnerabilities of Internet Surface Servers
a. Scan your organization's IP range from outside the network. Make sure all exposed IP / ports are as you expected.
b. Make sure automatic security updates are enabled for your exposed services. If any of your services (i.e web servers) does not have this feature, consider replacing it with a similar service with this feature.
LATERAL MOVEMENT:
1. Firewalls and Windows Update
Enable firewalls on all your workstations and servers. Make sure Windows Update is enabled. In this way, your machines are protected against the latest vulnerabilities and less prone to lateral movement techniques. Microsoft constantly updates its security policies and firewall rules.
A good example is to disable the remote creation of processes using the 'at' command.
2. Endpoint Protection
Endpoint protection works. Beyond blocking the techniques of traditional hackers, some of them also have defense against ransomware and protect your data from encryption.
3. Network Segmentation
You ideally want to minimize the risk of impact on your industrial network when exposed to a ransomware attack.
a. If possible, separate the IT network from the OT network segment. Monitor and limit access between segments.
b. Use different management servers for OT and IT networks (Windows domains etc.). In this way, compromising the IT domain will not compromise the OT domain.
4. Constant Network Monitoring
A constant network monitoring platform (we are aware of a good one) will help you identify threats while analyzing network traffic and in this way, you will be able to see the big picture of things going on in your network.
5. Data Offloading
Monitor your network for any unusual outbound traffic. Daily user activity should not generate more than nearly 200 MB / day of upload link activity per user.
HOW CAN SCADAfence HELP?
We offer the SCADAfence platform which serves as a comprehensive solution created to protect industrial organizations like yours against industrial cyberattacks (including ransomware). Furthermore, it helps you follow international safety standards aong its built-in features. Some are as follows:
• Asset Management
• Network Maps
• Traffic Analyzers
These tools help you carry out better network segmentation in your organization, ensure that your firewalls function properly and that every device in the OT network communicates only with the target with which it should be communicating. Moreover, you can detect assets that are not where they should be. I.e: forgotten assets in the DMZ.
Meantime, the platform which is the highest rated OT and IoT security platform monitors network traffic for any threats, including the ones involved in typical ransomware attacks. And for example:
• Security breaches are sent over the network.
• Lateral movement attempts by means of the latest techniques.
• Network scanning and network discovery.
In case of any security violation, the detailed warnings and alerts of SCADEfence will ensure you to get such threats under control as soon as possible.
Ultimately, we develop this tool to help industrial organizations comprehend the attack surfaces, carry out effective segmentation and continuous network monitoring for any malicious or anomalous activity.
VİDEO: ANATOMY OF THE TARGETED RANSOMWARE ATTACK
We want to share the true story of our latest incident response to an industrial ransomware cyberattack with you.
Incident response team of SCADAfence help companies in case of cyber security-related emergencies. In this video, we will review a recent incident response event we attended. This study has been published to help organizations plan their events and reduce the impacts of industrial ransomware on their networks.
Halten Sie Ihre Informationen auf dem neuesten Stand
Abonnieren Sie den Newsletter, um über die aktualisierten Informationen von OTD Bilişim informiert zu werden.






