


Choose from a complete portfolio of solutions designed to protect your applications, infrastructure and data centers.
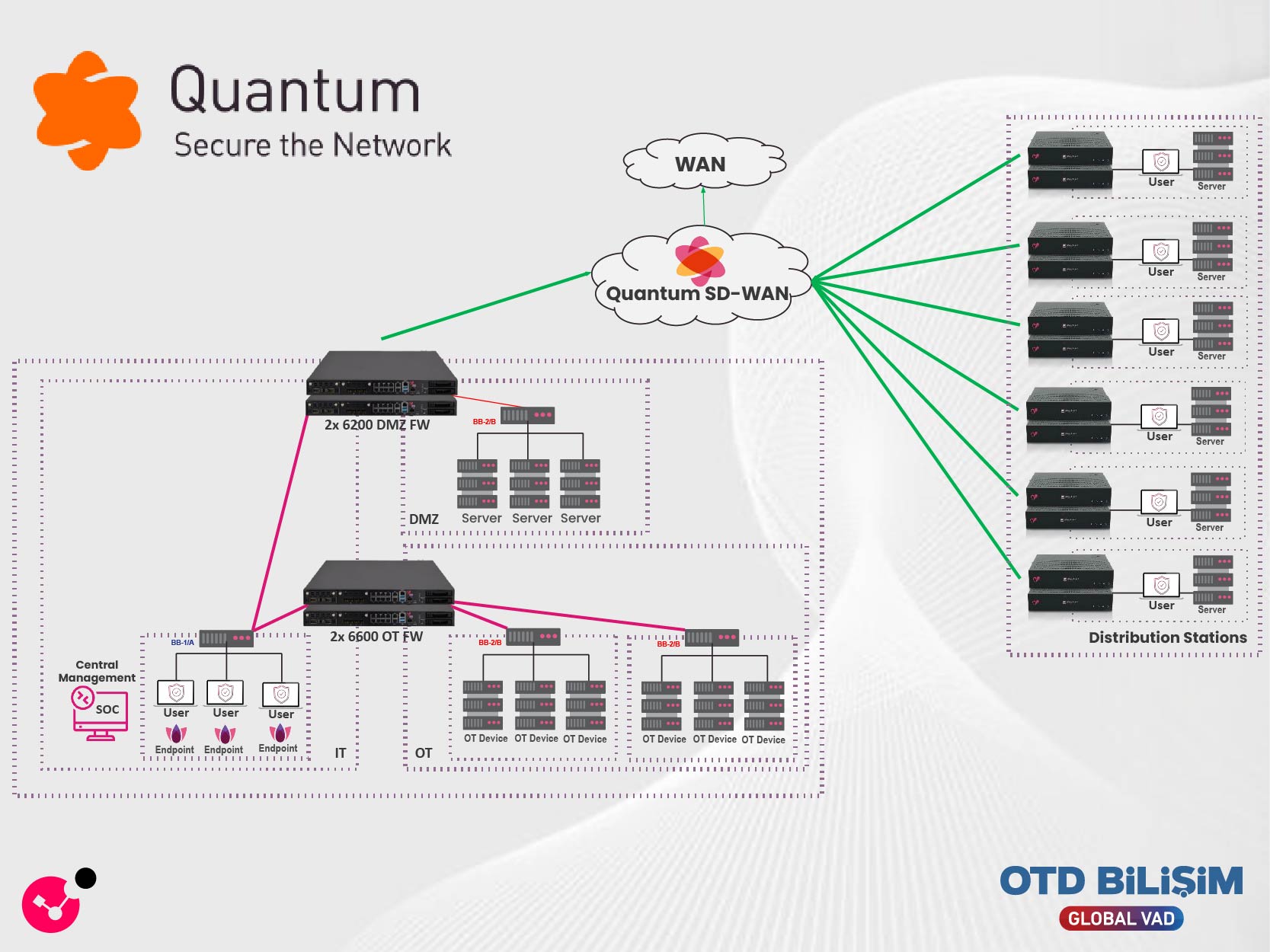
Check Point Quantum is a high-performance family of security solutions designed to protect enterprise networks, data centers, and connected devices against next-generation threats. It is equipped with advanced protection modules such as next-generation firewall (NGFW) capabilities, IPS, Anti-Bot, Anti-Virus, and threat emulation. It offers specialized solutions for large-scale enterprises and industrial facilities. The Quantum family stands out with its performance-oriented hardware, flexible scalability, IoT / OT security, and centralized management advantages. All devices are centrally managed through Check Point’s SmartConsole and Infinity Management infrastructure, providing a consistent and easy-to-manage security architecture.

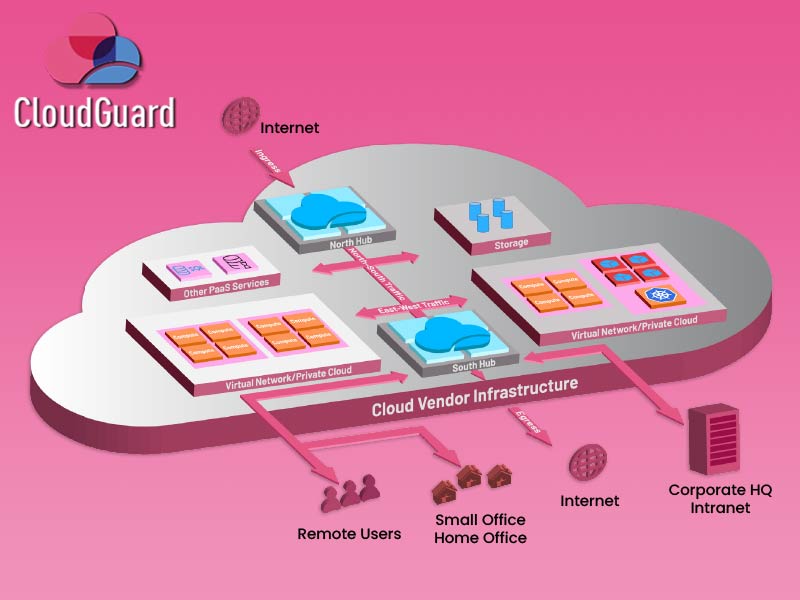
Check Point CloudGuard, kurumların kullandığı genel, özel ve hibrit bulut ortamlarını uçtan uca korumak için geliştirilmiş kapsamlı bir güvenlik çözüm ailesidir. AWS, Azure, Google Cloud, Kubernetes gibi yaygın bulut platformlarını destekler ve konfigürasyon hataları, güvenlik açıkları ve yetkisiz erişimleri önceden tespit ederek proaktif koruma sağlar. DevOps süreçlerine entegre olarak sürekli güvenlik sunması, otomatik görünürlük sağlaması ve uyumluluk denetimlerini desteklemesi en önemli avantajlarıdır. CloudGuard sayesinde şirketler bulut ortamlarını hem tehditlere karşı güvence altına alır hem de regülasyonlara uyumluluğu kolaylıkla yerine getirir.
CloudGuard WAF: Web uygulamalarını hedef alan SQL injection, XSS ve benzeri saldırılara karşı koruma sağlayarak uygulamaların güvenliğini garanti altına alır. Gerçek zamanlı tehdit önleme ile iş sürekliliğini korur ve düzenleyici standartların gerektirdiği güvenlik seviyelerini sağlar.
CloudGuard Network Security: Bulut tabanlı ağ güvenliği sunan bu çözüm, Next Generation Firewall, IPS, Anti-Bot ve tehdit önleme özelliklerini bulut ortamına taşır. VPC ve VNET trafiğini denetleyerek yetkisiz erişimleri ve saldırıları engeller, kurumların ağ içi ve dışı trafiğini bütünsel olarak korur.
CloudGuard CNAPP: Bulut yerleşimi ve yapılandırma güvenliğini sağlar. Yanlış yapılandırmaları ve güvenlik açıklarını tespit ederek bulut mimarisini en güvenli şekilde optimize eder, sürekli risk değerlendirmesi ile güvenlik açıklarını kapatır.
CloudGuard Posture Management: Bulut güvenlik durumu yönetimi (CSPM) ile tüm bulut varlıklarını sürekli izler, riskleri görünür hale getirir ve uyumluluk raporları sunar. Yanlış yapılandırmaları tespit eder ve KVKK, GDPR, ISO 27001 gibi regülasyonlarla uyumu destekler.
CloudGuard Code Security: Yazılım geliştirme sürecine entegre güvenlik sağlar. Kod analizleri ile güvenlik açıklarını build sürecinde tespit eder, geliştiricilere anında uyarılar sunar ve güvenli yazılım üretimini kolaylaştırır. Böylece potansiyel zafiyetler üretim ortamına taşınmadan engellenir.
CloudGuard Workload: Bulut iş yüklerini (sanal makineler, konteynerler, serverless yapılar) gelişmiş tehditlere karşı korur. Mikro segmentasyon ve davranış analizi ile hassas verileri güvence altına alır, tüm iş yüklerinde proaktif bir güvenlik katmanı oluşturur.
CloudGuard Developer Security: Geliştiricilerin kullandığı araçlarla entegre çalışarak güvenliği yazılım geliştirme sürecine dahil eder. CI / CD süreçlerinde güvenlik açıklarını otomatik olarak tespit eder ve böylece güvenlik, uygulamanın en başından itibaren doğal bir parçası haline gelir.
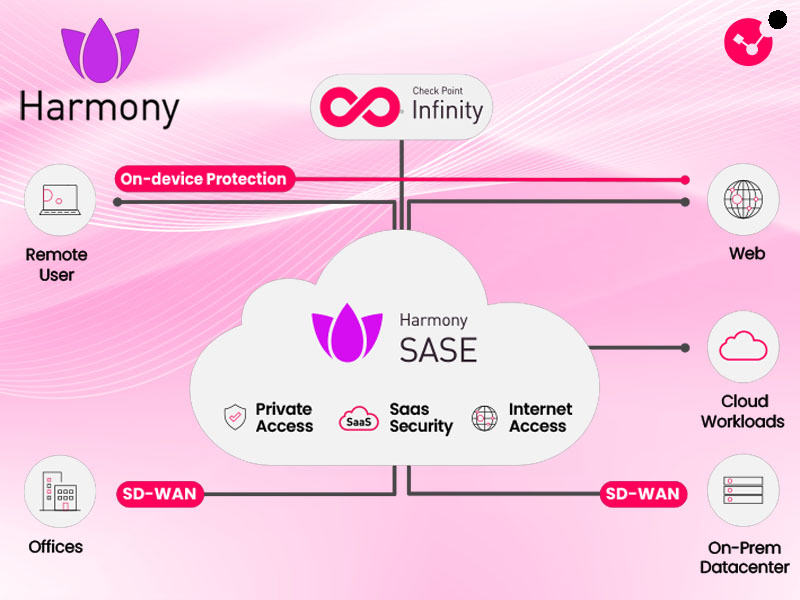
Check Point Harmony is an end-to-end cybersecurity solution family developed to ensure the security of employees and devices across all touchpoints in the modern business environment. With its Zero Trust approach, it grants access only to authorized users and devices, blocking threats across multiple interaction points. Managed from a single console, the platform provides advanced protection for email, web, endpoints, mobile devices, SaaS applications, and browsers.
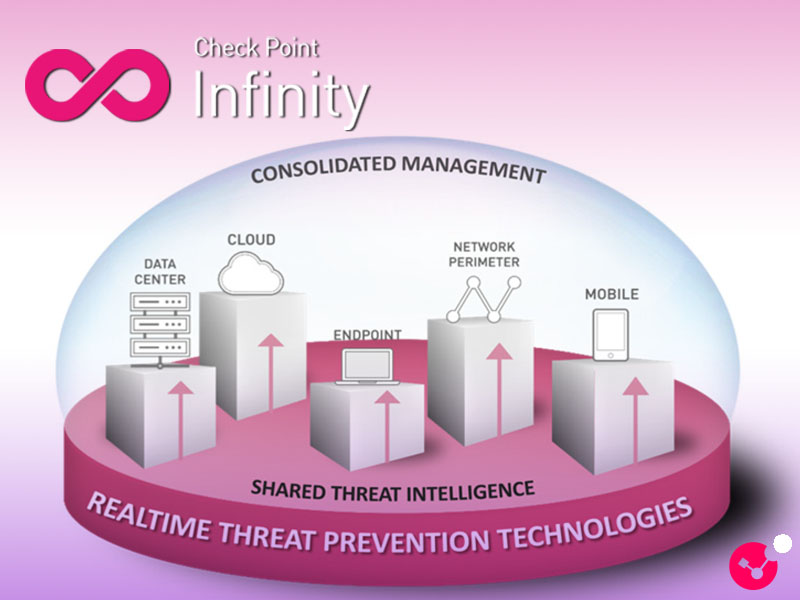
Check Point Infinity is an AI-powered, cloud-based cybersecurity platform designed to unify an organization’s security needs across different components such as network, cloud, endpoint, mobile, and IoT — all under a single framework to reduce complexity. Instead of the traditional “one product – one function” approach, Infinity is built on the concept of “one platform – multiple security controls.” Consisting of multiple integrated layers, the platform aims to address all enterprise security needs end to end.
Secure the Network component is designed to protect an organization’s network traffic, data centers, perimeter, and branch connections. In this context, the Quantum product family provides robust protection through security gateways, firewalls, and mesh configurations that support advanced network topologies.
Secure the Cloud component secures virtual machines, applications, workloads, and cloud-based network traffic running in cloud environments. At this layer, CloudGuard products take the lead, offering high-level visibility and threat protection across both hybrid and multi-cloud architectures.
Secure the Workspace component focuses on the user side, covering working environments such as email, mobile devices, endpoints, and SaaS applications. With the Harmony product suite, endpoint, mobile, email, and collaboration tool security is ensured, safeguarding users’ daily operations.
Secure Operations component enhances threat visibility across all these layers, consolidating data sharing, analysis, automation, and response processes. Here, Infinity Core Services come into play — enabling organizations to efficiently manage their security operations through technologies such as XDR, Playblocks (automation and orchestration tool), ThreatCloud AI, AI Copilot, and the centralized management interface Infinity Portal.
Ensure the Right Access with Zero Trust


Aim for Zero Risk with AI-Powered Prevention


Eliminate Threats with Multi-Layered Protection

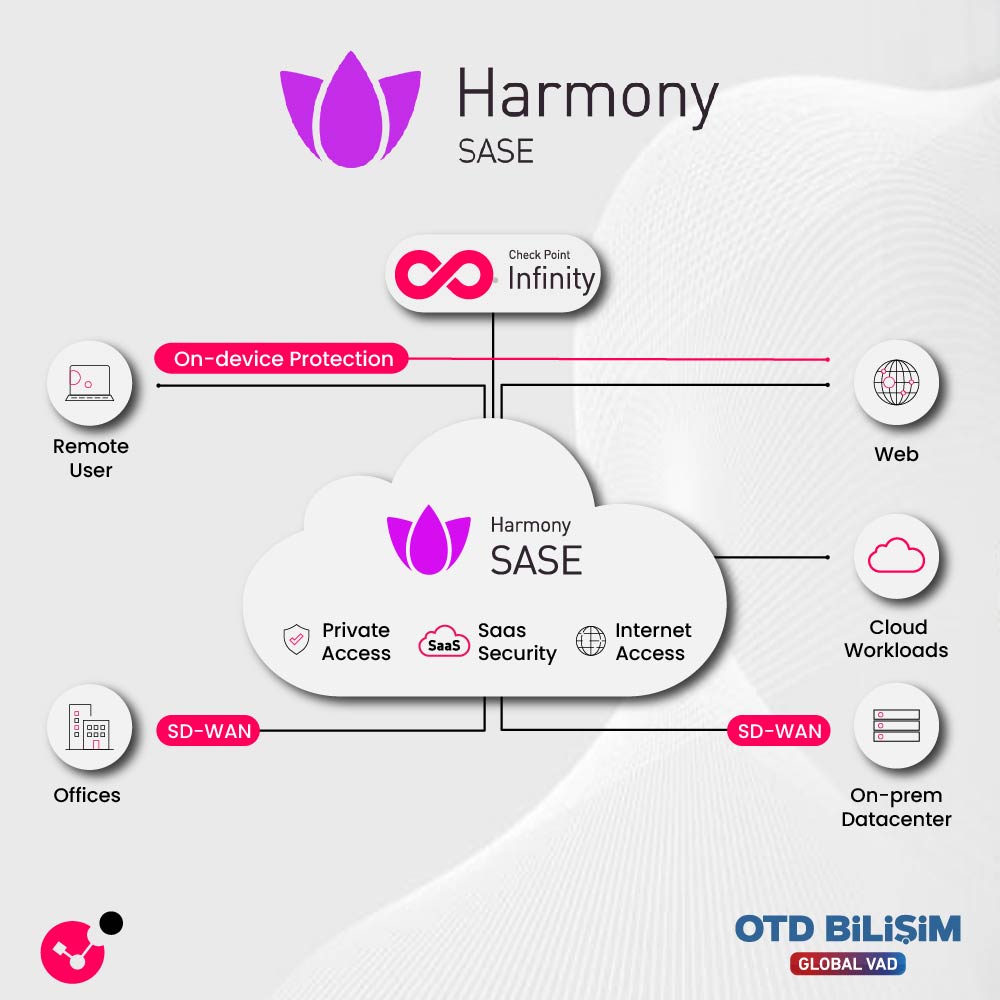
Harmony SASE enables users to securely and rapidly access corporate resources from anywhere. By combining networking and security into a single cloud-based service, it enhances performance while reducing management costs. It provides centralized policy control for branches, remote workers, and cloud-based applications, ensuring seamless, continuous security.
ZTNA follows the “never trust, always verify” principle, allowing users to access only the applications they need. Compared to traditional VPNs, it offers much more granular access control and, combined with identity authentication and device security checks, prevents data breaches and unauthorized access.
Infinity ThreatCloud AI elevates organizational security to the highest level through AI-powered threat intelligence. Fed by data from over 150,000 connected networks and millions of endpoints, the system rapidly detects and prevents unknown malware and Zero-Day phishing attempts with its advanced detection engines. Compared to traditional methods, it blocks significantly more attacks, providing a prevention-focused defense that successfully stops complex threats such as DNS-based attacks and command-and-control (C2) attempts.
Operating as a unified intelligence hub across the network, cloud, user access, and operations layers, it delivers a more proactive security approach, reduces operational burden, and maximizes the efficiency of security investments.
CloudGuard protects your workloads, applications, and data running on platforms such as AWS, Azure, Google Cloud, and many others against the most advanced threats. It enables centralized management of multi-cloud environments, ensuring continuous compliance and protection through automated security posture control and real-time threat prevention.
Secure SD-WAN places security at the core while optimizing all network traffic—from branch offices to data centers. With intelligent routing, automated failover, and performance optimization for over 10,000 applications, it delivers seamless connectivity. Its integrated protection against Zero-Day attacks, phishing, and ransomware keeps your organization both fast and secure.
Harmony Email & Collaboration blocks phishing, ransomware, and account takeover attempts targeting collaboration platforms such as Microsoft 365, Google Workspace, and Slack. Powered by AI and machine learning–based threat analysis, it detects even the most sophisticated attacks. Without disrupting users’ daily workflows, it provides end-to-end protection for your email and communication channels.
Harmony Endpoint protects your desktop and mobile devices against ransomware, phishing, malware, and data leaks. With advanced threat prevention and automated detection capabilities, it delivers the highest level of endpoint security without compromising the user experience.
IoT Protect provides visibility into connected smart devices and safeguards them against ransomware and botnet-based attacks. It delivers an advanced security layer specifically designed for critical infrastructure and industrial environments.
For the Latest Innovations in Network, Cloud and User / Access Security