In BT & OT (EKS) critical infrastructure, visibility, continuous monitoring, operational continuity, measurability of network performance, and cybersecurity assurance are the core goals every organization strives to achieve. Garland Technology, with its developed Secure Packet Mirroring Technology, ensures 360° visibility, leaving no blind spots in your network. The BT & OT (EKS) Cybersecurity Intelligence SoC network, which is parallel to your network, not only manages current threats but also proactively controls potential future risks. Garland Technology offers the most reliable, cost-effective, easily deployable, and scalable solutions in the industry. With its Active / Passive Network TAP and Network Packet Broker products, it provides 100% packet visibility to your security tools, eliminates operational downtimes, and helps you build a strategic network security infrastructure. Thus, your organization achieves full visibility in its security network structure and attains uninterrupted operational continuity, increasing the value of your network.




100% Network Visibility for Security and Monitoring Solutions
Garland Technology Network TAPs provide 100% visibility by passively or actively replicating network traffic and sending it to security and monitoring solutions. This ensures no packet loss, eliminates blind spots, and prevents delivery issues at SPAN/Mirror points. With real-time traffic replication, security tools are continuously fed accurate and complete data, which helps with early detection of threats and maintaining operational continuity. Active TAPs offer functions such as regeneration, aggregation, and filtering, while Passive TAPs provide uninterrupted monitoring without requiring power.
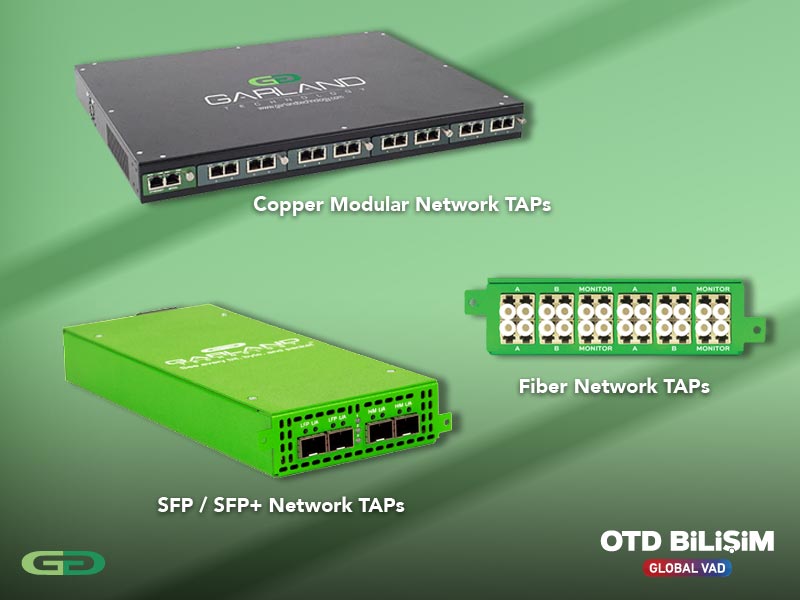
Garland Network Packet Brokers collect, filter, and optimize incoming traffic from different connections, correctly directing it to security and monitoring tools. This ensures that the tools are not exposed to unnecessary traffic and prevents the loss of critical packets. By making your security and monitoring infrastructure more efficient, continuous, and scalable, it maximizes both performance and return on investment.
Fly Away Kit Models: A lightweight and compact Network Packet Broker device specifically designed for portable cybersecurity solutions in field conditions. It offers quick setup and portability, providing reliable visibility in harsh environments, field operations, or emergency situations. Ideal for military and disaster scenarios.

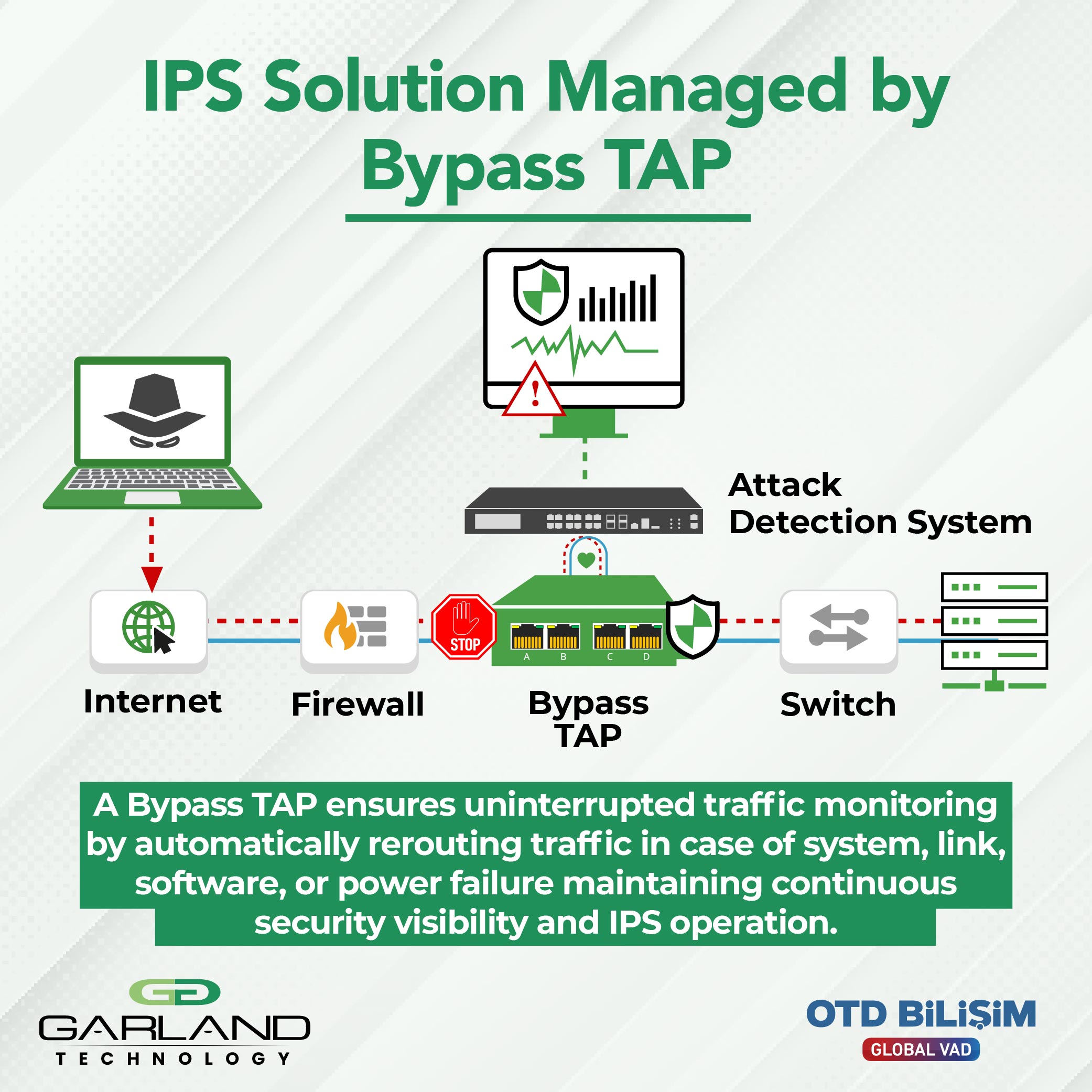
Garland Technology's Inline Bypass TAPs are designed to ensure the reliable operation of inline bypass security tools (IPS, WAF, FW, etc.) while maintaining network continuity. These solutions bypass traffic flow with zero latency when a security tool fails or requires maintenance, allowing the network to continue functioning without interruption. Additionally, they direct traffic to both security and monitoring tools simultaneously, offering maximum visibility and performance optimization. While preserving network continuity, they enhance the efficiency of security tools, make encrypted traffic visible, and maximize your return on investment.
• EdgeSafe (Portable & Modular): A portable and compact bypass solution that maximizes network uptime. It ensures continuous operation even if the inline security tool fails, providing fast problem resolution with support for 1G and 10G. It allows security devices to operate without network interruptions. Even if the security tool fails, traffic flow remains uninterrupted.

Inline Packet Broker solutions are designed to manage network traffic securely, seamlessly, and efficiently. These solutions enhance network visibility by ensuring that security and monitoring tools are fed with the most accurate traffic, improving operational efficiency and optimizing infrastructure costs.
Hardware Data Diode provides strong protection against cyber attacks by ensuring one-way flow in network traffic. By allowing data to be sent to monitoring tools only in the outbound direction through the SPAN port, it completely eliminates the risk of external access or return traffic to your network. This ensures compliance, uninterrupted operation, and full visibility in critical infrastructures and OT environments. Hardware-based data diodes allow Ethernet packets to flow only in one direction, enhancing visibility and defense while preventing cyber threats from penetrating back into the network.



100% Visibility, Uninterrupted Operation


Build Your Cyber Intelligence Network


Build Your Cyber Intelligence Network

Although internal bypass add-ons in IPS solutions may work in some failure scenarios, due to being software-based, they cannot close additional security vulnerabilities and do not provide the flexibility required during maintenance. Garland Technology's Bypass TAP solutions overcome these limitations, continuously ensuring the reliability of inline devices such as IPS, WAF, or firewall. Updates, patches, or troubleshooting processes easily allow you to take devices offline, thereby minimizing network downtime. Additionally, by eliminating single points of failure, it secures traffic flow and optimizes the performance of inline devices. This approach enables organizations to maintain operational continuity and makes their security strategies more resilient and scalable.
IDS solutions analyze network traffic by simply listening and require accurate data copies for reliable results. However, data obtained from SPAN ports often lead to security vulnerabilities due to packet losses, manipulations, or hidden threats. Garland Technology's Network TAP solutions provide complete data flow to IDS tools by replicating packets with 100% accuracy. Bidirectional traffic copies transmit both physical errors and offer the flexibility to direct the same data to multiple destinations. Especially when an IDS needs to monitor multiple network segments, TAPs, when used with Packet Broker solutions, organize the data, optimize security detection, and prevent critical threats from being overlooked. This way, organizations gain maximum efficiency from their IDS solutions with blind-spot-free visibility.
Known as the "Bypass Key", EdgeSafe Bypass TAP ensures the reliable management of inline devices such as IPS, WAF, or firewalls without causing network interruptions. Garland Technology’s modular design eliminates single points of failure, providing uninterrupted operation and secure traffic flow. Through Inline life cycle management, the safe deployment of new devices, the application of patches and updates, or the execution of maintenance processes are possible without affecting network performance. With its scalable architecture and high reliability, EdgeSafe solutions stand out as a critical component in organizations' BT security strategies and ensure operational continuity.
A network TAP provides full visibility by copying every bit, byte, and packet in your network. However, most of the time, security or monitoring tools do not need the entire traffic; they only need to see the parts relevant to their function. For example, a VoIP tool only needs to monitor voice traffic, while an analytics tool may want to track specific protocols. At this point, Garland Technology’s port filtering feature filters out unnecessary data and directs only the traffic that the tools require. This prevents monitor ports from being overloaded, improves the performance of the tools, and makes operational processes more efficient. The filtered and organized traffic is then forwarded to the security or monitoring tools when needed, enhancing both network visibility and security effectiveness to the highest level.
The energy sector, one of the most critical components of infrastructures worldwide, requires the highest security standards. Garland Technology’s Hardware Data Diode solutions ensure one-way traffic flow, protecting control and management systems from external attacks. With this structure, data is transmitted only in the secure direction, while reverse traffic is physically blocked, preventing cyber threats from infiltrating the network. This approach, combined with rugged designs tailored for industrial environments, guarantees both operational continuity and regulatory compliance for energy companies, while securing the reliability of critical infrastructures in the long term.
By integrating Garland Technology’s Bypass TAP into your network, you can guarantee the uninterrupted flow of network traffic even if inline security devices (firewall, IPS / IPS, DDoS protection, etc.) fail or require maintenance. The Bypass TAP continuously monitors the status of inline devices with "heartbeat" packets; upon detecting a failure, it automatically and instantly disables the device, redirecting traffic to ensure operational continuity. This approach eliminates single points of failure, allows maintenance and updates to be performed without shutting down the network, and enables you to perform validation/optimization before bringing inline devices back online. With its modular and tool-compatible design, it offers seamless integration with existing security infrastructures, resulting in fewer disruptions, faster interventions, and higher availability.
The financial sector, where sensitive data such as subscriber information, account details, and business transactions are processed, is among the most targeted by cyberattacks. For this reason, 360-degree visibility of network traffic and continuous monitoring are critically important. Garland Technology’s Packet Broker solutions optimize the data collected by TAPs and transmit it fully to monitoring and analysis platforms. This prevents delays, errors, and security vulnerabilities caused by dropped packets, allowing threats to be detected and addressed immediately. For financial institutions, this means both meeting compliance requirements and proactively preventing attacks that could lead to billions of dollars in losses. The Packet Broker enhances security in critical financial infrastructures while ensuring performance and operational continuity.
Telecommunication infrastructures, especially with the transition to 5G, must meet higher speed, lower latency, and uninterrupted connectivity demands. Traditional Tier-3 architectures have evolved into Tier-4 architectures with the addition of aggregator solutions, enabling reliable transmission of traffic to monitoring platforms in hybrid networks using both copper and fiber. Garland Technology’s solutions offer advanced features such as load balancing, level 2-4 filtering, GRE, VxLAN, ERSPAN tunneling technologies, time stamping, and packet slicing in these next-generation networks. Additionally, with deduplication, unnecessary data load is reduced, maximizing both performance and monitoring accuracy. For telecom and 5G network operators, this means securely, regularly, and error-free processing of billions of packets; ultimately providing uninterrupted service quality and a robust security infrastructure.
The defense sector requires the highest level of security, resilience, and uninterrupted visibility. The "Zero Trust" cybersecurity model and corporate defense structures such as JEDI form the foundation of this approach, and Garland Technology provides tailored solutions to meet these requirements. Military-Grade TAP devices, designed to withstand harsh environmental conditions, ensure bi-directional traffic flow without packet loss over 10/100/1000 M copper connections and never compromise on reliability in the field. This allows defense institutions to manage their networks in both scalable and high-performance ways, detecting threats immediately and ensuring operational continuity. Garland solutions provide a critical foundation for the efficiency, security, and error-free monitoring needed by sensitive defense operations.
For the Latest Innovations in Network Visibility, Packet Routing and Critical Infrastructure Security