


To fully realize the value of your security investments and minimize risks, SafeBreach’s Exposure Validation Platform offers services with two powerful components: Validate and Propagate.
Continuously Test Your Security Controls
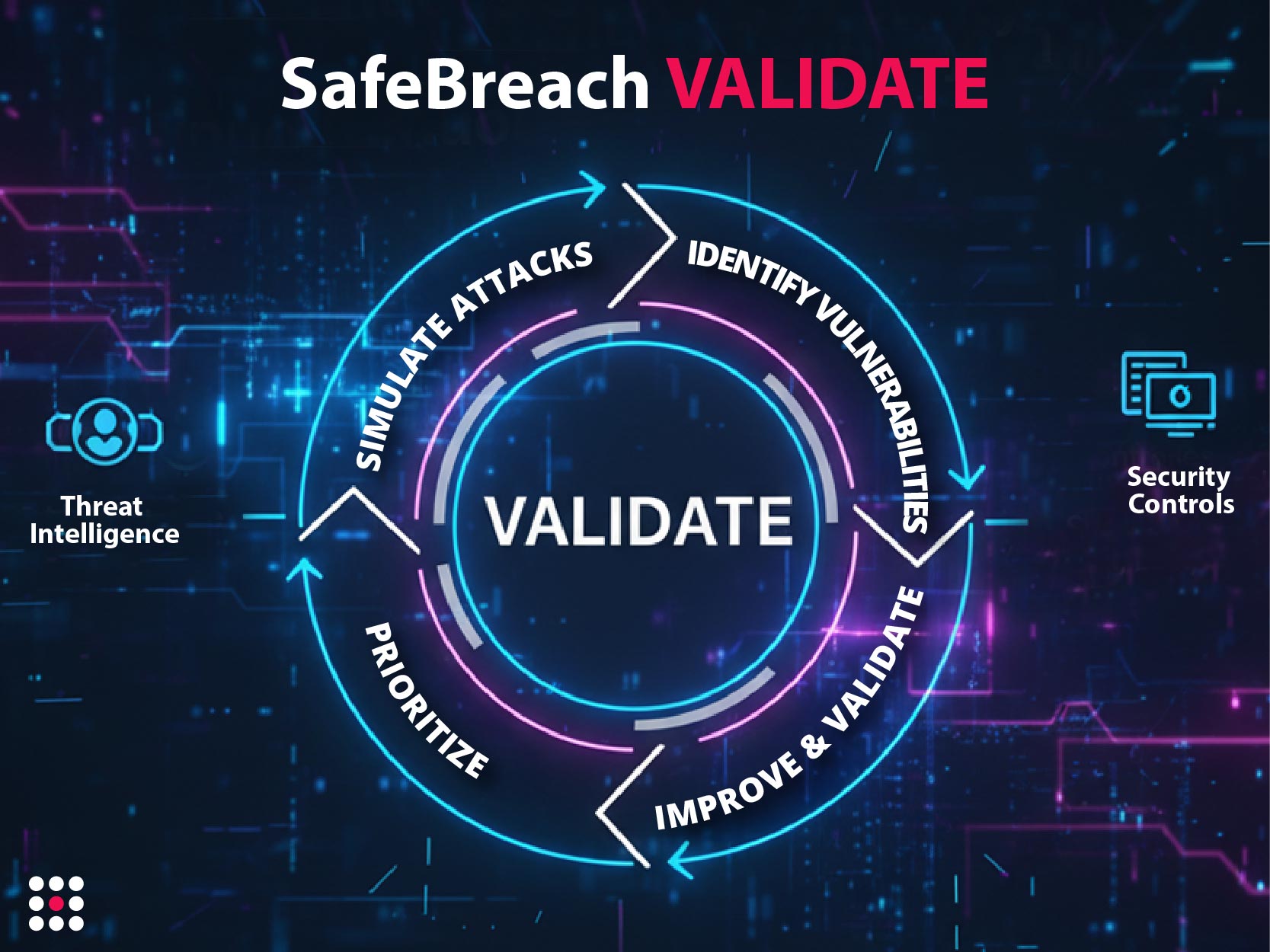
Validate continuously tests your systems against real threats using the patented Hacker’s Playbook™ with over 30,000 attack techniques. You can create custom attacks based on your own threat intelligence and clearly measure how resilient your controls are.
See Your Attack Surface, Measure Your Risk
Each test analyzes your organization's security posture according to MITRE ATT&CK® categories. You can easily see which threat groups, techniques, and system vulnerabilities you are weak against, and make strategic decisions based on data.
Accelerate Remediation
Validate clearly identifies the root cause of failed simulations and which control was insufficient. This allows security teams to quickly take action with relevant units, drastically reducing patching and remediation times.
Optimize Detection Engineering
You can automatically test your custom detection rules with known attack methods. SIEM and SOAR systems validate your alert cycle end-to-end, reduce false positives, and ensure continuous security operations.
Make Data-Driven Decisions
Validate provides measurable insights into control effectiveness, threat exposure, and cyber risk. This allows organizations to clearly see the return on security investments, set operational priorities, and allocate resources most effectively.
Secure, Scalable, and Enterprise-Ready Design
It has a unique technology that simulates the behavior of malware without ever running actual harmful software. Tests are run without risking system stability or data integrity. It works in a scalable manner across cloud, on-premise, or hybrid environments.
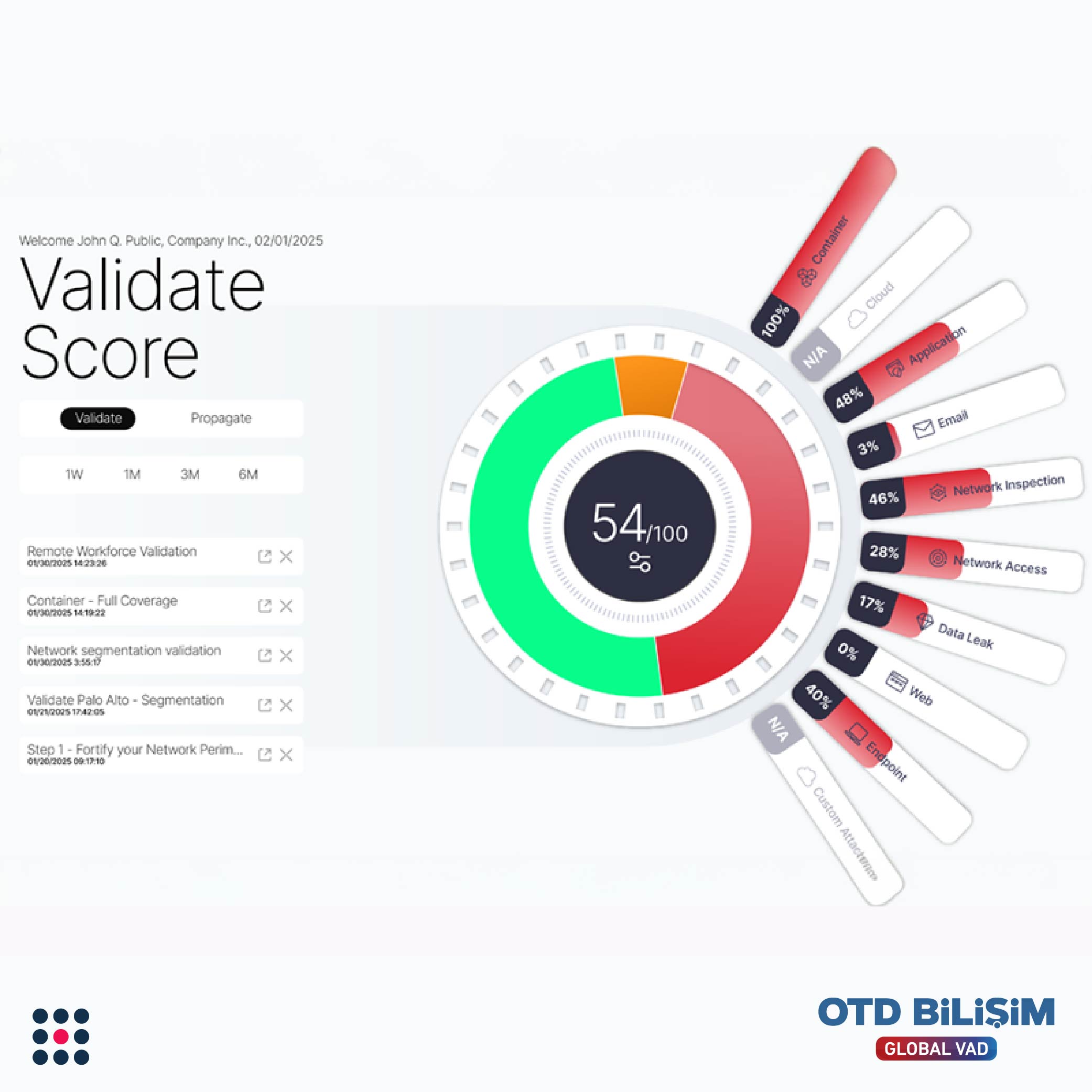
Comprehensive Reporting and Dashboards
Flexible dashboards and customizable reports allow you to instantly view your security posture. Ideal for tracking progress, comparing risks, and presenting clear, measurable results to upper management.
Continuous Compliance and Security Validation
Validate ensures continuous verification of control effectiveness for frameworks like PCI DSS, NIST CSF, and ISO 27001. With MITRE ATT&CK® mapping, it clearly shows which threat categories have vulnerabilities during audits. It provides continuously updated security evidence, rather than just saying "tested within the year."
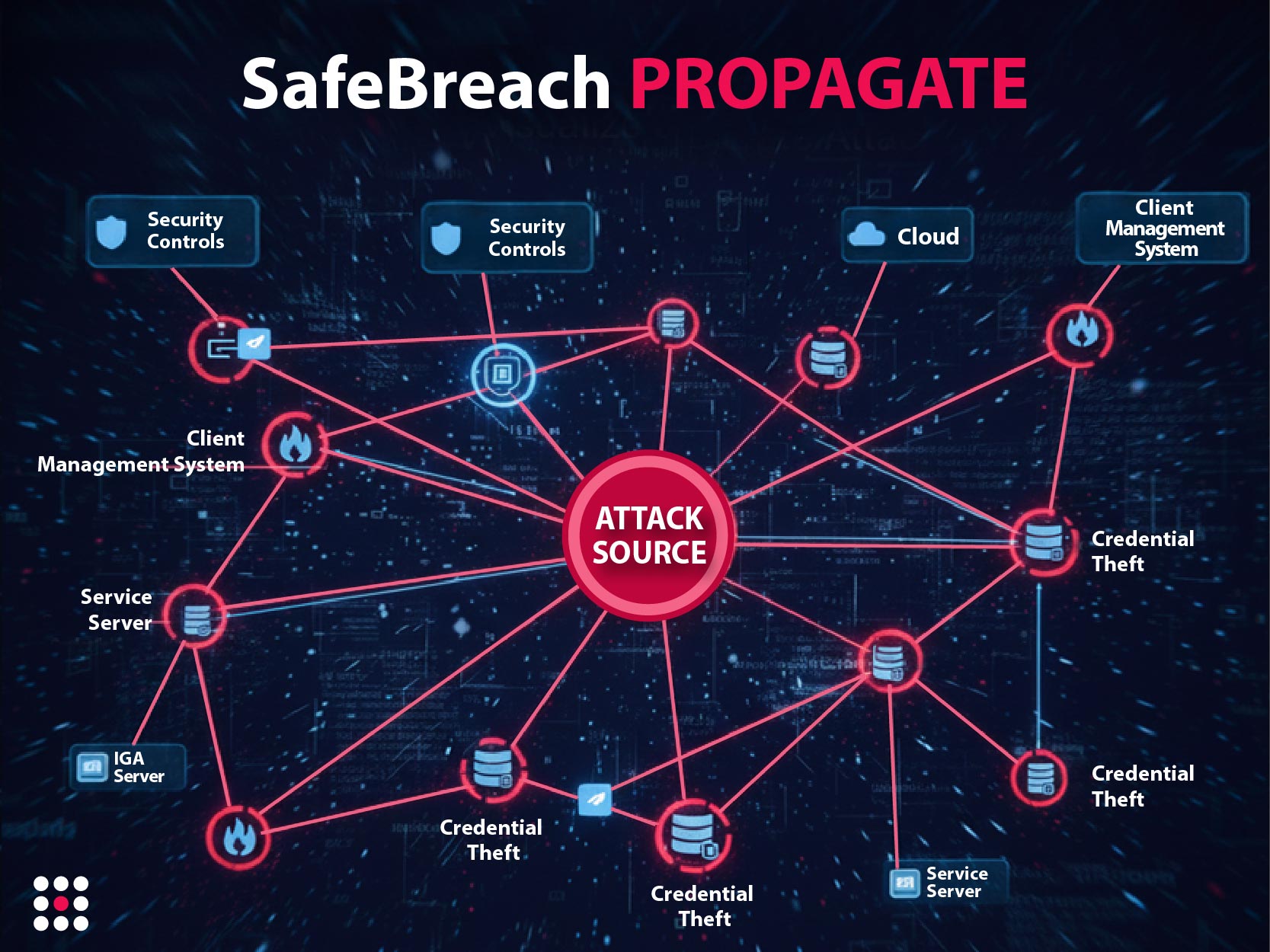
Measure Your Resilience with Continuous Attack Simulations


Test Your Defense with MITRE ATT&CK Tactics


Prioritize Security Vulnerabilities Correctly

For the Latest Innovations in Breach & Attack Simulation, Threat Visibility, and Cyber Resilience