“Full Visibility, Full Control in OT (ICS) Security.”
With the advent of Industry 4.0, OT devices began integrating with SCADA and ERP systems, bringing the need for continuous data exchange and remote access. This data flow—enabled by IoT and IIoT equipment, sensors, and industrial protocols—increases efficiency in smart factories while simultaneously amplifying cybersecurity risks.
Honeywell Forge Cyber Security is a comprehensive platform that delivers end-to-end visibility, asset management, secure integration, and advanced threat detection. With centralized management, advanced analytics, and a scalable architecture, it ensures the security of SCADA systems—enabling operations to run continuously, securely, and in compliance with standards.
Thus, enterprises can confidently continue their digital transformation journey while enhancing both business continuity and operational efficiency



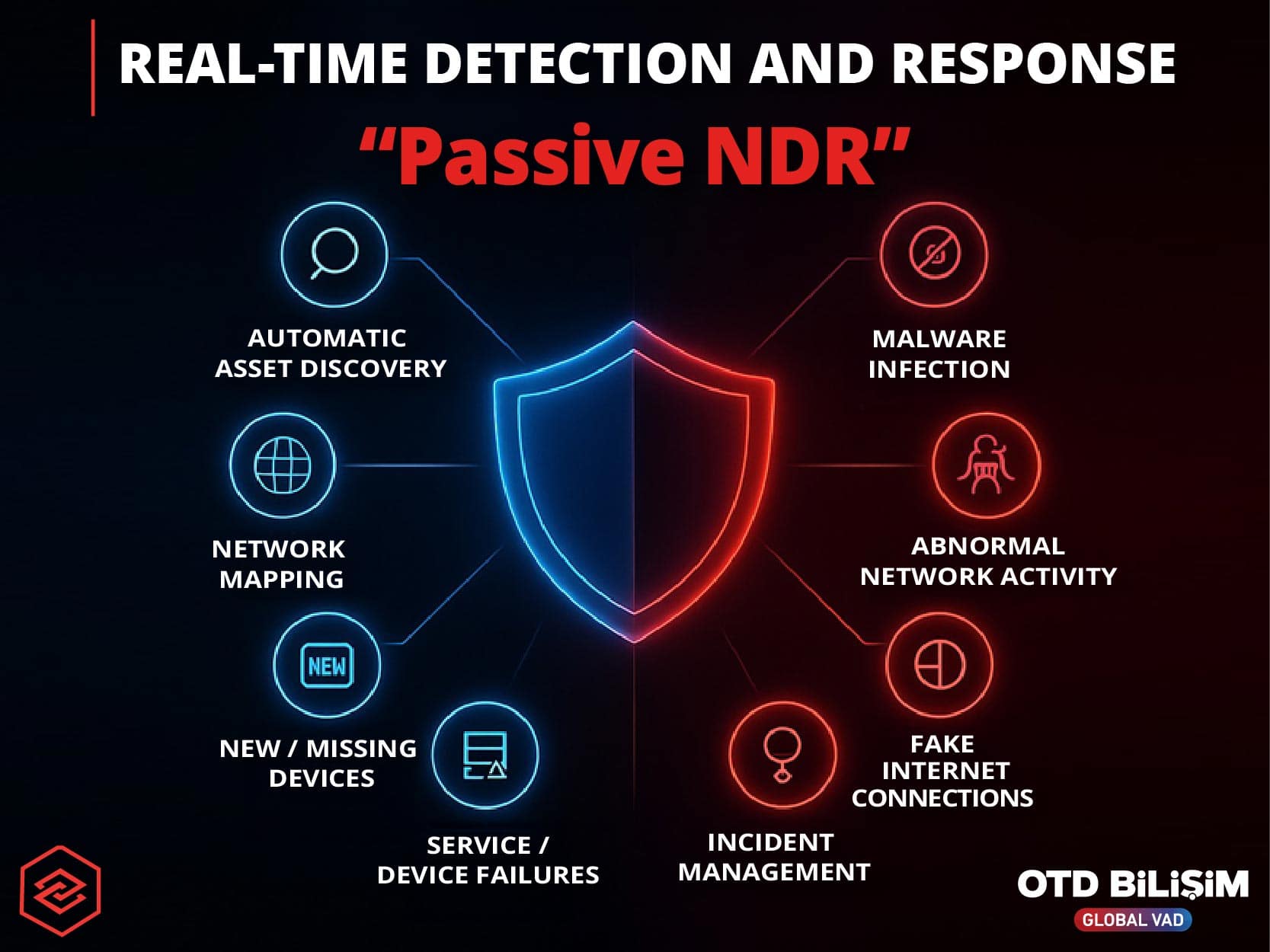
Full Visibility and Security Against Cyber Threats in Industrial Networks with Passive NDR and IDS
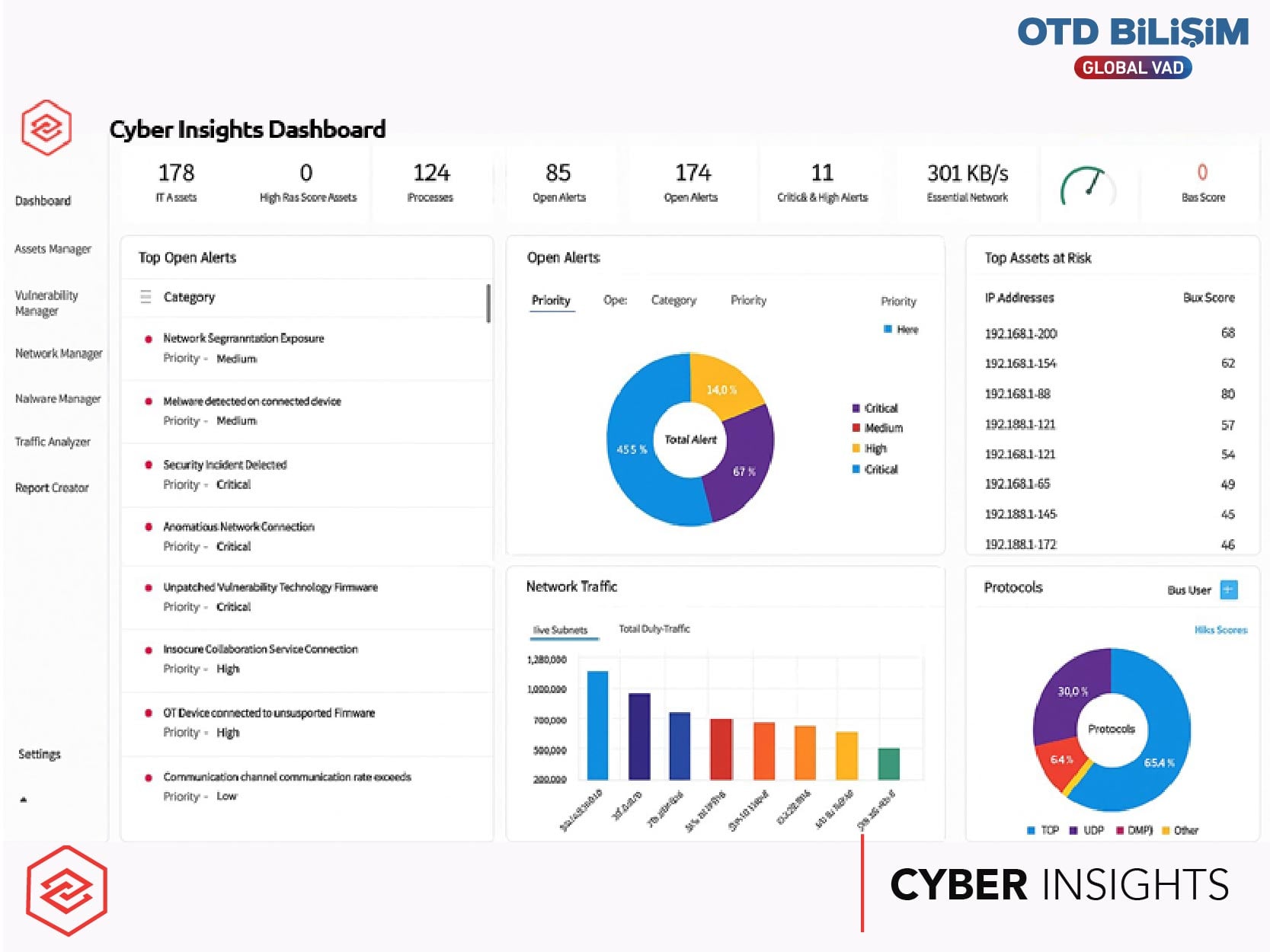
In today's increasingly complex energy, industrial, and building automation networks, visibility and security are more critical than ever. Honeywell Cyber Insights provides powerful protection for your OT environments and SCADA infrastructures by monitoring them almost in real-time, including asset discovery, vulnerability management, and detection of malicious activities. Thanks to its open and flexible architecture, it offers seamless integration with your existing process control systems, SCADA solutions, and building management technologies. This enables end-to-end visibility, reduces risks, ensures operational continuity, and secures your critical infrastructures for the future. Additionally, with advanced cybersecurity intelligence capabilities, it employs the "Passive NDR" (Network Detection and Response) approach to perform real-time, in-depth analysis, reduce the threat surface, and provide proactive security.
Visibility and Analysis: Cyber Insights automatically discovers all assets in your OT networks, inventories them, and makes them visible with detailed network maps. Abnormal network activities, unauthorized access, and vulnerabilities are quickly detected, allowing operational risks to be identified in advance.
Risk Mitigation: Asset risk scores, CVSS, and known vulnerabilities (CVE / KEV) are correlated to prioritize the most critical threats. Automated security reports, risk analysis, and threat assessment views accelerate decision-making and strengthen your security posture.
Operational Efficiency: Provides deep visibility into industrial commands and suspicious communications. With SIEM and SOAR integration, alert management is simplified, and sensorless deployment support offers cost-effective remote monitoring options.
AI-Driven Detection and Response: AI-powered threat detection increases security with high accuracy and low false positives. Malicious software, abnormal traffic, and unauthorized OT commands are detected, visibility is provided, and security teams are quickly notified.
Flexible and Scalable Architecture: With RBAC support, it assigns specific access rights to different users and departments. Smart sensors are optimized for low bandwidth, and distributed processing ensures that data is analyzed locally, with only summaries and necessary results transmitted to the center. This reduces bandwidth usage, decreases delays, and ensures the system continues to operate reliably and sustainably at any scale.
Compliance and Reporting: Continuous monitoring of compliance with regulations and industry standards is facilitated with compliance measurement capabilities. Automated reports transparently present security vulnerabilities, risk levels, and remediation recommendations across the organization.
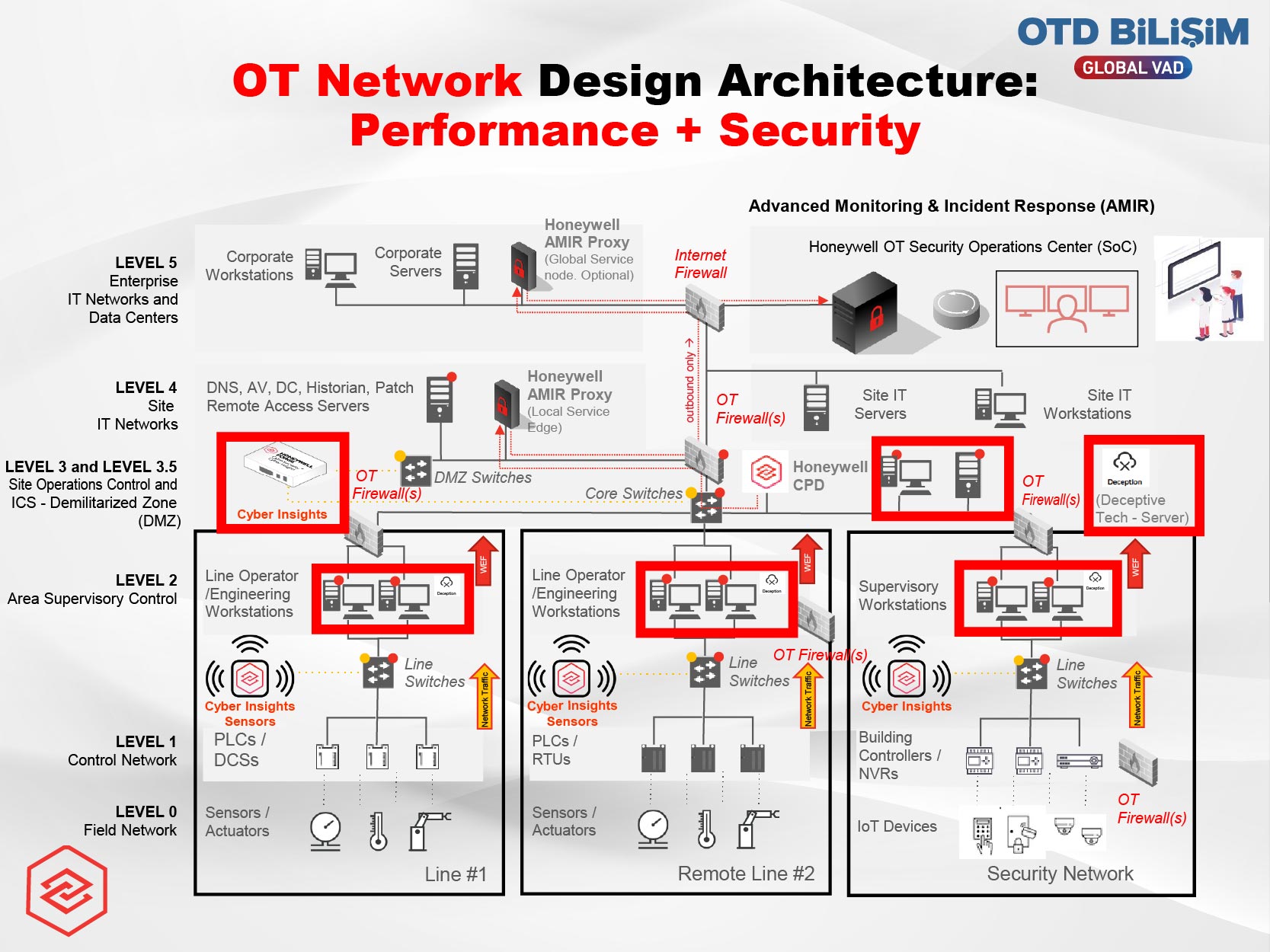
A next-generation cyber defense solution that combines artificial intelligence, OT intelligence, and a digital SoC approach against cyber threats targeting OT infrastructures. It detects threats, anomalous activities, and potential attacks at an early stage across OT assets. Through artificial intelligence and machine learning algorithms, anomaly detection is accelerated, false positives are reduced, and real threats are prioritized. Going beyond known signatures, it performs active analysis to uncover hidden and targeted threats, mitigating their impact through automated response. Acting like a digital SoC analyst, it enables security teams to transition to a proactive resilience model.
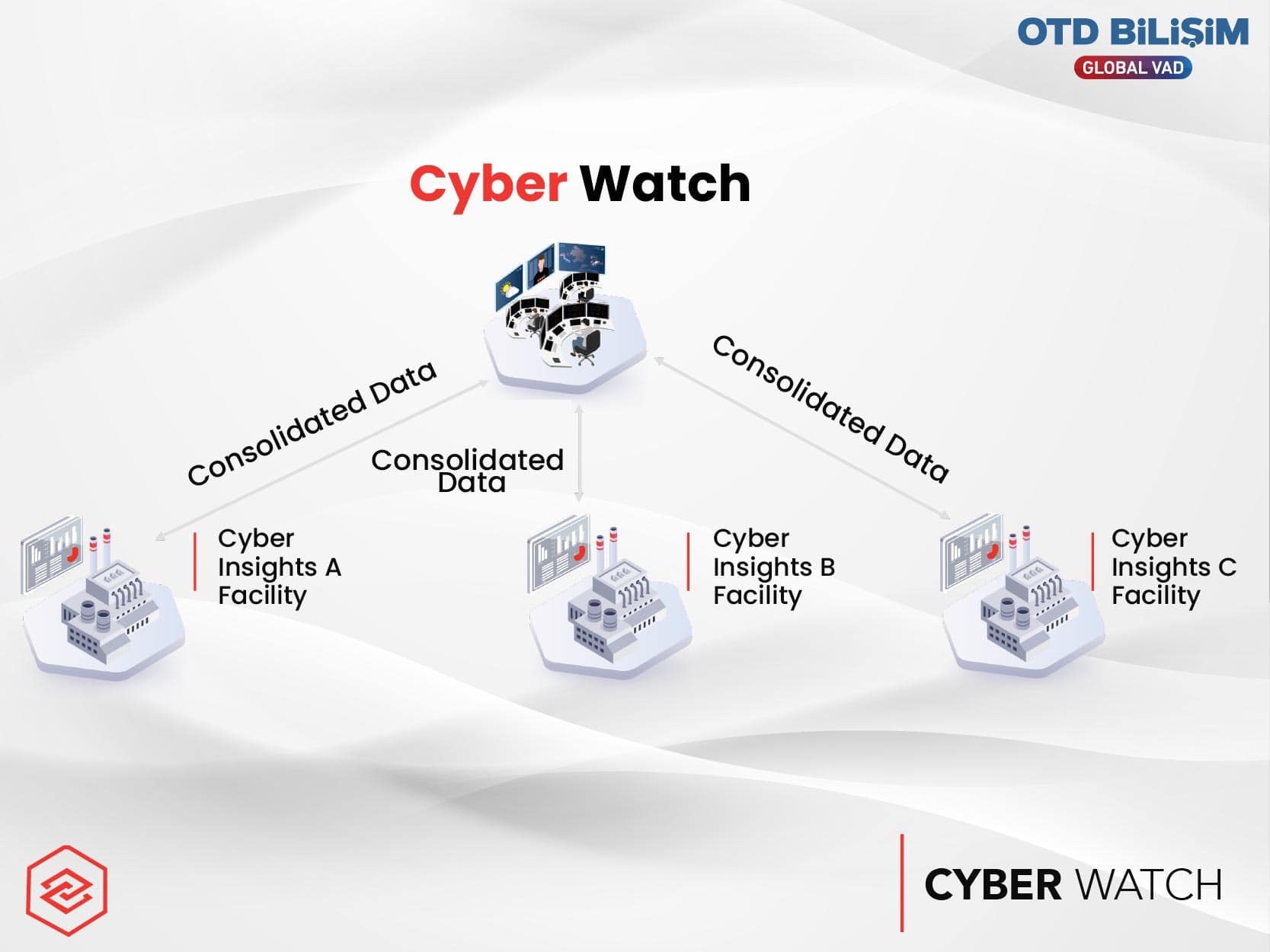
Honeywell Cyber Watch is designed to allow organizations to track their cybersecurity profiles globally. It provides comprehensive visibility and management through two different portals:
Multi-Site Portal: Provides visibility into cyber threats across multiple facilities. Supports hundreds of different locations through a central platform. It consolidates all asset inventory, traffic, and alert data, among other information collected from the facilities, into a single central location.
Governance Portal: Allows IT and audit departments to centrally define and monitor compliance with organizational policies. It supports OT standards and regulations (such as IEC 62443, NIST frameworks). Ensures compliance with internal policies; facilitates the implementation of common rules across facilities with best practices.
Honeywell Cyber Watch Governance is a powerful solution that enables organizations to centrally manage their OT cybersecurity policies and compliance statuses based on real data. This structure, designed specifically for CISOs and security leaders, allows for compliance reporting and measurement using up-to-date, real-time data obtained from networks.
The Governance Dashboard not only tracks compliance but also enables organizations to manage their cybersecurity strategies with data-driven decisions and take proactive measures against global threats.
Central Governance: Designed to remotely and continuously monitor the compliance of your fields with industry standards such as EPDK, NIS2, OTCC, SOCI, IEC 62443, NERC CIP, NIST, ISO 27001, and corporate policies.

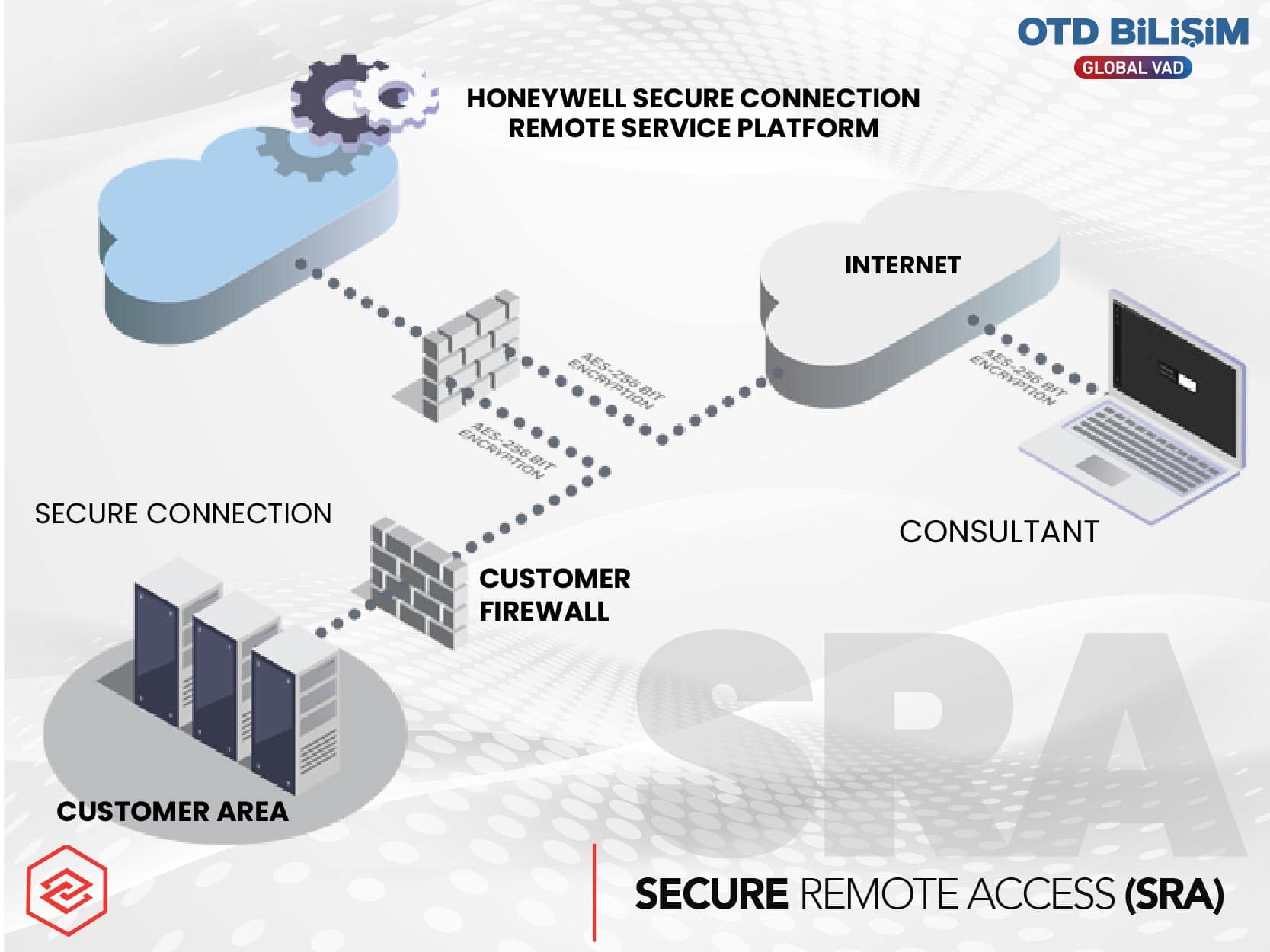
Honeywell Secure Remote Access ensures that only authorized personnel have access to process control systems, preserving data confidentiality and operational continuity. With a multi-layered security approach, it provides authentication, encryption, logging, and role-based authorization. Honeywell Secure Remote Access offers maximum security, flexibility, and operational efficiency for remote access to your facilities, meeting modern industrial security standards.
End-to-End Security: AES-256 encryption, two-factor authentication, and role-based authorization ensure that only the right person accesses critical systems at the right time.
Full Traceability: All access and security logs are retained for 180 days, ensuring transparency during audits.
Easy Management: Centralized server management simplifies monitoring and updating, while firewall configurations are streamlined.
Flexible Access Models: Supports different needs with options for one-time sessions (Session-Based), persistent agent-based access (Agent-Based), and temporary access (Host/Guest Pass).
Operational Efficiency: Multiple users can connect to the same session, solving problems faster and supporting continuous operation of the facilities.
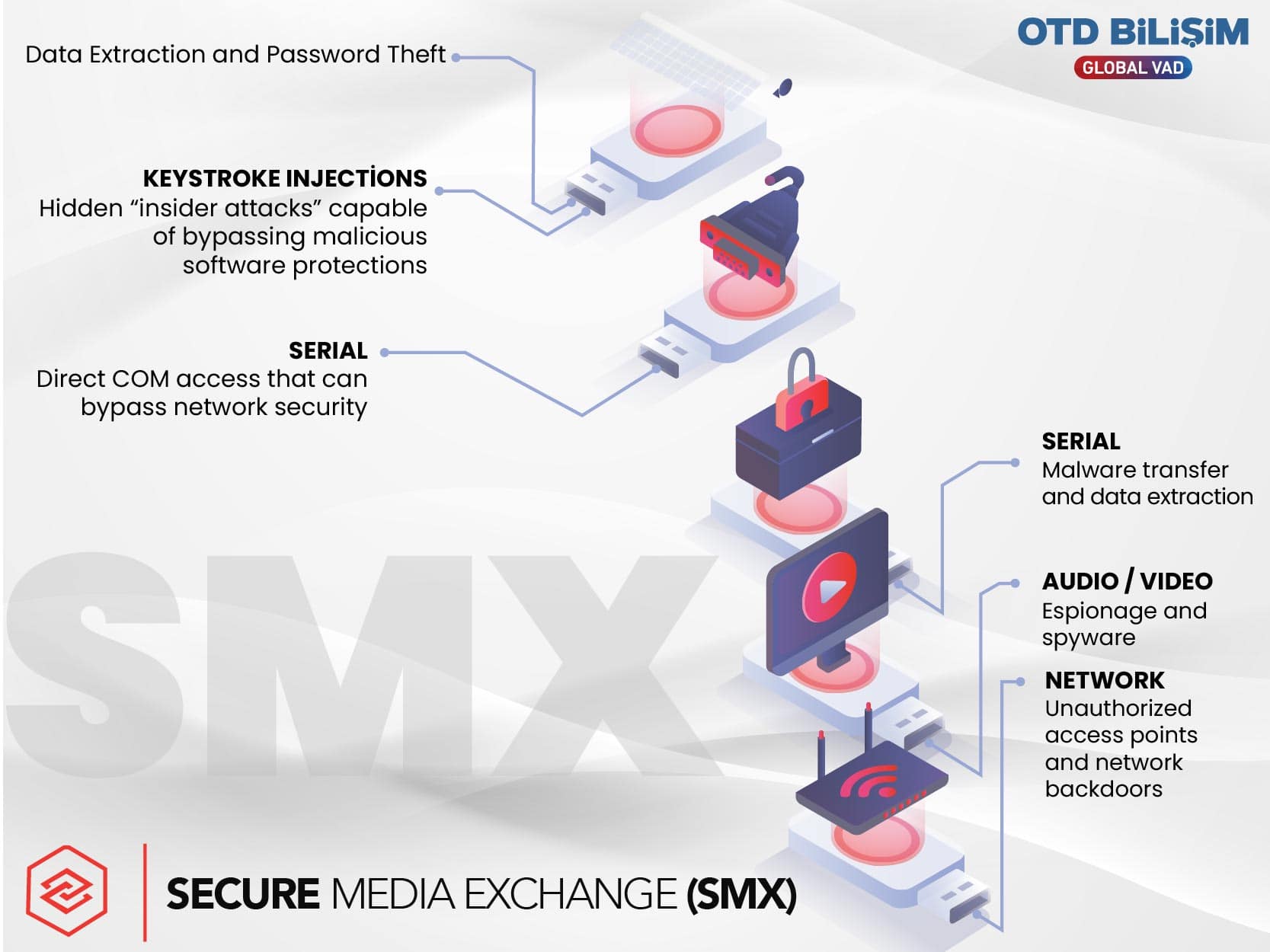
Honeywell SMX provides a corporate-level solution that reduces cybersecurity risks and operational disruptions by monitoring and logging removable media activities. Air-gapped systems offer scalable visibility and management across remote sites and multiple facilities.
Prevents Cyber Threats: Detects and blocks malicious software before USB devices can access critical infrastructure.
Secure Field Use: SMX Portable Scanner safely scans USB devices, even on systems with no internet access.
Continuous Protection Updates: Always stays up-to-date with the latest EKS threat intelligence provided by Honeywell’s GARD threat research team.
Compliance and Transparency: Complies with EPDK, ISA-99, IEC 62443, and NIST standards. Facilitates compliance audits by logging media activities.
Operational Continuity: Instead of banning USB usage, it secures it, ensuring both security and business continuity.

Proactive Defense, Uninterrupted Production


Monitor SCADA And OT Systems 24/7


Make Your OT Network Fully Visible


For the Latest Innovations in Critical Infrastructure, ICS, and Remote Access